Passkeys Unlocked: A Security Deep Dive
Changing threat landscape in authentication
Introduction to Passkeys
Authentication Today: Navigating a Maze of Passwords
Think about the last time you forgot a password. Frustrating, right? This small annoyance is a symptom of a larger problem in our online world. We're surrounded by passwords: they're the keys to our emails, social networks, and bank accounts. But as hackers get smarter and our digital lives grow more complex, passwords are starting to show their age. They're either too simple to be safe or too complex to remember.
What we need isn't another password; it's a new way to prove who we are online. A method that's secure but simple, where you don't have to memorize a string of characters or reset your password every time you forget it. It's time for a change, a shift towards something that makes our online lives easier and safer.
Understanding Authentication: Beyond Passwords
Ever had that moment where you're locked out of your account, trying every password combination you've ever used? We've all been there. It's not just annoying; it's a glaring sign that the traditional password system is faltering. Passwords are like the old locks on a modern digital door – they just don't fit anymore.
But what's beyond passwords? Imagine walking into your online accounts as easily as you enter your home, without fumbling for keys. That's where the future of authentication is headed – smarter, smoother, and a lot more secure. We're talking about systems that know it's you without needing a password, using methods that are not only cooler but a whole lot tougher for the bad guys to crack.
This new era of authentication is about ditching the outdated and embracing the new. It's about making security invisible yet unbreakable, where accessing your digital world is as natural as your morning coffee.
The Great Shift: From Passwords to Passkeys
Remember flip phones? They were cool until smartphones showed up. It's the same with passwords - they did their job, but now we're ready for something better. Well, it's time for a change. Enter Passkeys: a new, simpler way to secure our online lives. No more memorizing complex passwords; passkeys are here to make things easier and safer for everyone. We're not just replacing passwords; we're upgrading to a smarter, more secure way to protect our digital world.
Why now, though? Because everything around us is getting smarter and more connected. Our phones aren't just phones; they're lifelines to everything we do online. And with this smart, connected world comes the need for smarter security.
The change isn't just about keeping up with technology; it's about keeping up with us. We're online more than ever, managing more accounts, more data, and facing more risks. It's high time our authentication methods catch up. We need a system that's not just secure, but also fits into our fast-paced, interconnected lives.
Rising Popularity of Passkeys: A Tech Revolution
It's like when smartphones first hit the market - everyone wanted one. That's what's happening with passkeys. Big tech companies like Apple, Google, and Microsoft aren't just supporting passkeys, they're championing them. Why? Because they see the future. A future where logging in is as easy as unlocking your phone. These companies are integrating passkeys into their operating systems and browsers, making them a standard part of your digital experience. It's a big push, signaling a major shift from the era of passwords to a more secure, user-friendly future.
Under the Hood: How Passkeys Work
Imagine your online identity as a puzzle that only you can solve. That's the magic of passkeys. Technically, passkeys are based on a concept known as public key cryptography. It sounds complex, but here’s the simple version: when you create a passkey, your device generates two unique keys - one public and one private. The public key is like an address that you can share with others; the private key is like the secret code that only you know.
Every time you log in, your device uses this private key to prove your identity without actually revealing the key itself. It’s like showing ID without handing it over. This process ensures that even if someone intercepts your login attempt, they can't replicate it, because they don't have your private key. Plus, since there's no actual password to type in, there's nothing for hackers to steal the traditional way. It's a blend of simplicity and high-tech security, redefining how we protect our digital selves.
Delving into the technical details of passkeys requires a deeper look at their structure and operation:
Key Generation and Storage: When you create a passkey, your device generates a key pair using public key cryptography. This involves sophisticated algorithms like RSA or ECC (Elliptic Curve Cryptography). The private key, which proves your identity, is securely stored on your device, often in a hardware-based secure element for enhanced security. The public key, which can be shared safely, is stored by the website or service you're accessing.
Authentication Process: During authentication, the website requests a signature from your device. Your device then uses the private key to create this signature, which is unique for each login attempt. This signature, along with the public key, ensures your identity without transmitting the private key.
Security Protocols: Passkeys often use protocols like WebAuthn (Web Authentication), a web standard for secure authentication on the web, part of the FIDO2 specifications. WebAuthn allows servers to register and authenticate users using public key cryptography instead of passwords.
Cross-Device Synchronization: Some systems enable the synchronization of passkeys across devices through cloud services or other mechanisms, while maintaining strong encryption to protect the passkeys during transfer and storage.
Fallback Mechanisms: In case of device loss or failure, there are usually recovery methods in place, like linking the passkey to another device or using a backup authentication method.
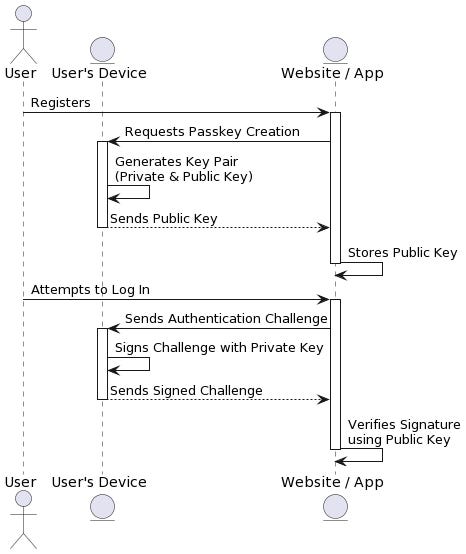
Here is a User’s journey and how passkeys are used -
Decoding Risks - Threat Modeling Passkeys
Phishing Attacks:
Passkeys enhance security against phishing compared to traditional passwords. WebAuthn-compliant browsers, essential for passkeys, implement several security checks like enforcing TLS and origin checks for credentials. These checks prevent credentials from being used on a different domain, significantly reducing the effectiveness of phishing attacks. Attackers would need to find a cross-site scripting (XSS) bug or a browser vulnerability to bypass these checks, which are high barriers to overcome.
Stolen Credentials:
Server-Side: If a server's credential database is compromised, the leaked credentials can't be exploited as no clear-text private key is shared with the server. This reduces the risk of attacks like dictionary attacks against reused credentials.
Client-Side: Private keys stored on user devices pose a different risk profile. The security of these keys depends on the device and its features. For instance, modern devices with Secure Element chips or hardware security keys offer better protection than older devices or those without such features. Therefore, the security of passkeys can vary based on the device used.
Account Takeover and Adding Credentials:
Passkeys make stealing credentials less feasible. However, attackers might look for logic vulnerabilities to add their credentials to a user account, achieving a similar effect as stealing credentials. This highlights the need for robust security measures in the account management and credential addition processes.
Relation to Multi-Factor Authentication (MFA):
Passkeys, in some cases, can function alongside or even replace MFA. For example, modern mobile phones and security keys can enforce multiple authentication factors when accessing passkeys. The suitability of passkeys as a replacement for MFA depends on the application's trust in the credential recovery process of the vendor (like Google or Apple) synchronizing the credentials. While passkeys are likely to remain a key defense for high-security applications, they could replace MFA in lower-security applications within a few years.
Here is an attack tree, what and how can attacker do to exploit -
Applications of Passkeys: Making Life Easier and Safer
Passkeys aren't just about logging in; they're changing the game in our everyday online adventures:
Online Banking: Imagine popping into your bank account as easily as you grab a coffee.
Social Media: It’s like having a VIP pass to your social circles, minus the password hassle.
Shopping Online: Shopping becomes a breeze when your secure login is just a tap away.
For businesses, passkeys are like having a digital bouncer for data security:
At the Office: They’re the new keycard for accessing all things work-related.
Client Confidentiality: Like a vault for client info, passkeys keep prying eyes out.
Compliance Regulations: Think of passkeys as the secret ingredient that keeps your business's security recipe in line with those tough industry standards.
Wrapping Up: The Future Is Keyless
As we close the chapter on passwords, passkeys are stepping into the spotlight. They're not just a new tool in our digital toolbox; they're reshaping how we think about online security. With tech giants leading the charge and innovative applications emerging, the future looks both keyless and promising. We're moving towards a world where online security is robust yet user-friendly, and passkeys are at the heart of this transformation. So, as we embrace this new digital era, let's bid farewell to password woes and welcome a smarter, safer way to live our online lives.